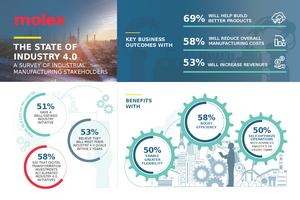
BGEN. The benefits of digitalization are well-known. Many businesses embracing Industry 4.0 have seen significant efficiency and productivity benefits while reducing costs. And this rapid growth is showing no signs of slowing down.
According to Markets and Markets, the industry 4.0 market is projected to grow from USD 64.9 billion in 2021 to USD 165.5 billion by 2026; it is expected to grow at a CAGR of 20.6% from 2021 to 2026. The key factors fuelling the growth of the industry 4.0 market include rapid adoption of Artificial Intelligence (AI) and Internet of Things (IoT) in the manufacturing sector, increasing demand for industrial robots in the pharmaceutical and medical device manufacturing industry, rising government investments in 3D printing and additive manufacturing, and growing adoption of blockchain technology in manufacturing.
Implemented correctly, digitalization can help industrial businesses transform their operations, with industrial control systems (ICSs) leading the charge. However, along with the benefits come the associated risks. Namely, security.
Security concerns
Protecting these crucial systems is big business. The ICS security market was valued at USD 106.68 billion in 2020 and is expected to reach USD 168.53 billion by 2026 at a CAGR of over 8.01% during the forecast period 2021 - 2026.
However, attacks are a constant threat. They can be varied, ranging from an ICS insider and common ransomware to more sophisticated ways such as vendor back door or hardware supply chain attacks. Stuxnet was one attack that made the headlines causing considerable damage to industrial companies. Others have gone unreported.
There are typically three types of attack:
Physical – hardware, network ports, switches, routers and USB ports. Such attacks are often difficult to conduct (gain access), present a higher risk of getting caught, and are relatively easy to secure against using physical barriers.
People – Manipulation, mistakes, phishing and social engineering. These attacks take time, effort and planning, but it is possible to target many potential victims quickly. It is also a larger threat when more people have access to systems. This type of attack is exceedingly difficult to defend.
Virtual – Hijacking, malware and software vulnerabilities. Often initially difficult to exploit, but once discovered they are extremely easy to attack. Software updates and firewalls offer reasonable protection
Mitigating the risks
The first thing to help reduce the risk of an attack is to reduce the attack surface, like putting a wall in front of a free kick. The attack surface describes the number of potential vulnerabilities or attack vectors available to an attacker.
For example, if there are a lot of computers connected to the internet all running common software which might not be up to date, there is a large attack surface. Similarly, if there are a number of people who have access to something that a cybercriminal wants to access, the people themselves represent a large attack surface.
Common software although usually well patched and secured can present a large attack surface, because once a vulnerability is known, there can be millions of potentially vulnerable systems. Bespoke software although potentially less well patched may present a smaller attack surface, because there may be only one or very few potential victims. and exploits will be more difficult to find since copies of the software may not be readily available.
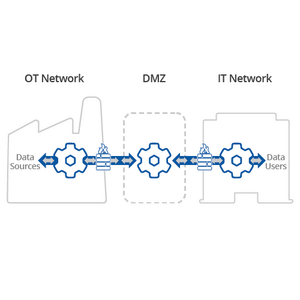
The good news is that most ICS deployments are to some degree protected against external attacks through physical security; secured physical access, "air-gap" separation of ICS equipment from IT and public networks, and few people with access to these systems.
This is not perfect however as the industry moves towards the convergence between IT and OT networks, and does not solve one of the main attack vectors which is via the people that operate the equipment. They potentially remain vulnerable to social engineering techniques and other forms of manipulation. Modern connected devices and open networks mean that airgaps are no longer a reliable means of security.
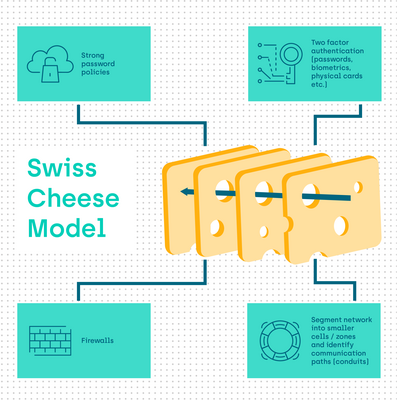
The "Swiss cheese” model
Defence in depth is an approach to cybersecurity which provides layers of protective systems and mechanisms. This approach (also known as the “Swiss cheese” model) builds defences in multiple layers so that a vulnerability in one layer does not automatically grant access at another.
Imagine your cybersecurity defence is a slice of Swiss cheese. It has holes in it and these holes represent ways an attacker can gain access. It is important to understand that no single layer can be 100% secure.
However, if you take several slices of Swiss cheese, each representing a different layer of security, and you arrange these so that the holes in the slices do not align, then where an attacker can get through one layer it is increasingly probable that another layer will stop them.
Additional layers that actively monitor and detect intrusion and threats coupled with regular testing to attempt unauthorised access further strengthen that model.
Check list
It is important that a cybersecurity plan should be designed following the IEC62443 principles. And the security plan should cover securing the devices, management and network. This includes:
Securing the devices (mechanical and software):
- Alarms and sensors (panels)
- Locking ports
- Procedures for using USB devices
Securing the management:
- Role based access (identification and authentication)
- Strong password policies
- Two factor authentication (passwords, biometrics, physical cards etc.)
Securing network communication:
- Firewalls
- VPNs
- Device management (enable/disable ports. Port security – monitor MAC addresses)
- Encryption (Common Industrial Protocol)
- Traffic filtering
- Segment network into smaller cells / zones and identify communication paths (conduits)
Into the future
While no system is 100% safe, taking a layered approach to security and regularly testing the system can help to significantly reduce the risk of attacks. This, alongside a comprehensive disaster recovery plan, will enable industrial companies to fully realise the potential of digitalisation while mitigating the security risks.
Simon Clarkson and Andy Marshall, senior digital managers at BGEN