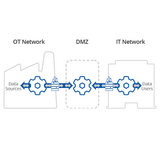
The increasing interconnectedness of processes provides industrial enterprises many opportunities to enhance their competitiveness. At the same time, this also results in new threats for data security. To address them successfully, safeguards must be extended into cyberspace, including both the Internet and other global networks, as well as all modern information and communication technology. But how can this goal be achieved?
The past has shown that mainly proprietary, manufacturer-specific data protocols are vulnerable to cyber attacks. The reason being that only a comparatively small group of people work on these protocols, unlike with the standardized ones. In order to achieve increased security against network attacks going forward, communication protocols that are specified as standard and freely accessible as RFCs (request for comments), for instance, should be implemented into products from the start. This is because these protocols have been very thoroughly reviewed by numerous experts and were developed from their inception with security in mind. They therefore offer the best possible security, benefiting the products and ultimately companies and processes as well.
In addition, companies need to talk openly about problems that have occurred in the area of cyber security. Discretion is of course initially necessary in such cases. After all, market partners, especially customers, shouldn't feel blindsided. At the same time, however, this period of discretion needs to be used to develop possible patches that remedy the security vulnerabilities. Furthermore, external communication should be prepared and coordinated with all stakeholders. Finally, the vulnerability should be announced, coordinated and accompanied by security patches.
Ostrich-Like Policies Lead to a Dead End
This approach causes difficulties for many companies, especially in the industrial sector. The reason can be attributed to the fact that the issue of cyber security hasn't been on their radar for very long, which is why the necessary ability to control issues of cyber security themselves is often insufficient or missing altogether. They often have their heads buried in the sand, acting with the mentality that they just shouldn't talk about it or else more problems will come their way. However, this attitude can quickly backfire if external specialists discover the vulnerability in question - either accidentally or purposefully - and then make it public, not only are the problems now out in the open, but there is also the added problem of a significant loss of corporate image.
By contrast, companies that address vulnerabilities offensively can gain credibility. Given the complexity of many products, it is obvious that issues can never be completely ruled out despite extensive testing prior to their launch. It's much more important to tackle these problems quickly with the customer in mind - in other words, demonstrate competence and control.
Closing the Digital Barn Door
What else can be done in terms of cyber security? This question presents a tough hurdle for medium-sized companies in particular. After all, the measures required and the development of the necessary expertise are expensive. Yet, a comprehensive solution comprising complete protection against all possible network attacks doesn't have to be in place from the beginning. Cyber security is more of an ongoing process. First, you should become aware of potential threats. In Germany, for example, many mid-sized companies - some of the world's best in their industries - can be as wide open as a digital barn door when it comes to protecting their technological know-how. After the most serious weaknesses have been identified, some initial steps should be taken to implement cyber security. In addition, a continuous improvement process should be implemented, just as in quality management, in which the level of security is gradually raised to an ever higher level.
Furthermore, it would be helpful to create a platform where both the government and the business community could discuss the topic of cyber security together. This approach can only be successful if all relevant stakeholders participate. Experience has shown that when this is not the case, parallel platforms may form leading to turf wars that end up benefiting no one. Secondly, duties must be clearly divided between the government and the business community. One example is the National Institute of Standards and Technology (NIST), which is a part of the U.S. Department of Commerce. NIST publicly announces the development of new cryptographic algorithms, which are then developed by the business community. In other words, the governmental agency gives targeted incentives to companies to find innovative solutions, thus, automatically developing their expertise in cyber security. Germany should adopt this approach so that it too can successfully be safeguarded from the threats of cyberspace.
Conclusion
Due to the ever increasing interconnectedness of processes, cyber security is becoming a decisive factor for economic success. Therefore, companies need to take action before it's too late by developing safe products, openly communicating problems, and securely integrating cyber security into a corporate culture that is continually improving itself. In addition, the government and the business community have a duty to provide standardized solutions because this is the only way that all market participants can benefit equally.