One of the important things that we've observed in the recent past is an increased number of attacks, cyber-attacks, ransomware attacks, phishing attacks, and thus, compromises on networks and operations. That can happen in any industry, from meat packaging, industrial facilities, power utilities, chemical plants, oil processing plants, gas processing, plants, and more.
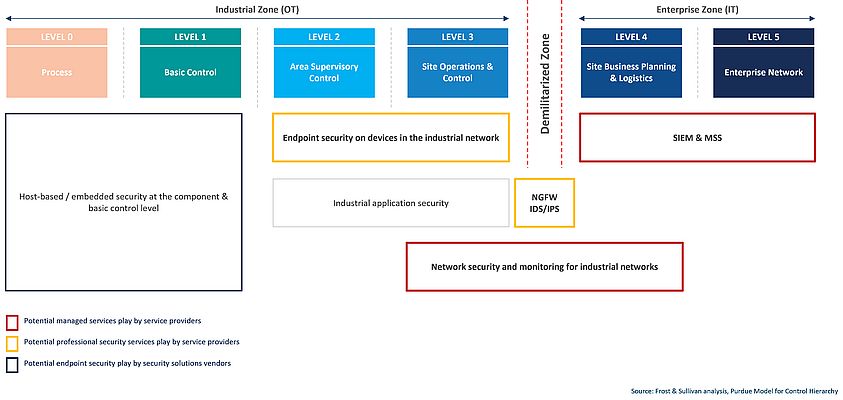
Ram Ramasamy from Frost and Sullivan introduced the key topics such as the cost related to the lack of preparedness, the customers’ need, and customers inactivity around enforcing security policies. The two aspects that really stand out among Ram Ramasamy are securing the OT network and its convergence to the IT network. The second important thing is data privacy and data protection, which is often overlooked, especially when dealing with very sensitive information.
How to drive sustainability in business with AI and security? How can customers consistently maintain their security posture on an ongoing basis?
Among Jens Kulikowski from Secunet, “the first step is transparency to see in the customer view what is available in the existing installed base and the assets in the production environment. The second step is, what would you tell us here on machines that are originally not designed as IT security devices?”. He continued: “And for that, we have decided it makes no sense to make a machine secure by itself. That makes more sense to have an additional device, hold that device up to date from IoT security perspective, and make that edge device compatible with the legacy stack. It's much easier, much more efficient and much more sustainable. And these devices can be updated. The benefits we also see here by using technology is long-term availability.”
Marcus Schmeisser then put the light on the G+D example: “We at G+D produce banknotes sorting machines fraught for print works, for banknote printing companies, for central banks and for nearly everyone in the cash cycle commercial banks. The machines are operated in a highly secure environment. Physical security access to these machines is very much restricted. And when it comes to connectivity, these machines were simply not connected in a completely independent way from the rest of the world in the past. Thus, the request came up: We want to connect these machines into our internal network to our internal data center.”
A couple of interesting things to observe here were how easy it was to convert an Industry 2.0 machine to an Industry 4.0 machine by using a simple edge connect device and secondly, how G+D has been able to drive new revenue streams with the customers.
What is Intel's role in easing the journey and time to market for application development for participants like Capgemini, and what value are they bringing to customers?
Ricky Watts from Intel commented: “Intel does a lot of these things about this fusion of OT and IT. This fusion runs on Intel platforms. We're trying to drive the right attributes that we need to bring out in the fabric and expose them up into the architectures that we're building as well. We work with end customers looking at those use cases and understanding what they are trying to do, their security concerns, and how we can adapt our technologies and work together with our viable ecosystem. We try to understand all layers working within the ecosystem, aligning to the customer need and driving the assets that we want to bring through to enable this IT OT integration, with security as a number one priority”.
Jacques Mezhrahid concluded with the collaboration between Capgemini and Intel: “We created together a platform to address every aspect of security and the way to shell the different models, keep the control on the different assets, and to be able to manage these kinds of assets. We worked together with Intel to provide our customers with a generic platform using standards based on OPC UA. The data model is key in preserving the interoperability between the system and between the different OEMs or suppliers working in the integration system. Right now, we are now in the second phase to auditing the level of security and to manage private keys to be able to generate our proper certificate to manage the right level of security and to be compliant with the regulatory side in France.”
Security absolutely has to be at the foundation of a solution that is deployed in the manufacturing space.
You can review this webinar at this link.